Refresh Token
Is to renew the Access Token in case the access token is expired.
Refresh token can be random ID or JWT
- Normally we use Random ID so that we can store in a database and manually invalidate. Which give us more secure way to control
- Also we can consider Refresh token rotation to keep the token changing
Considering the following flow:
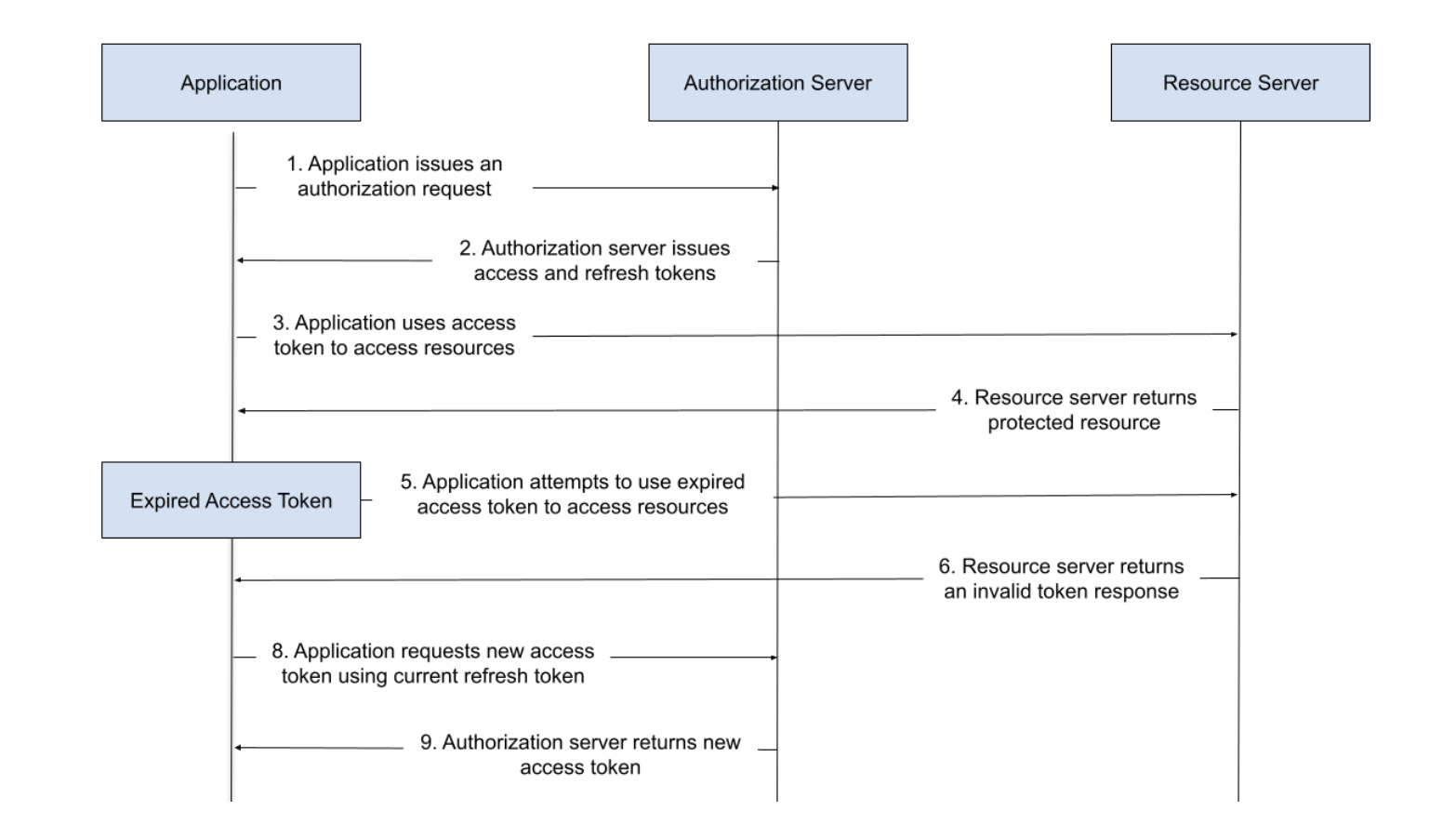
- Application authorise
- Server returns
access_tokenandrefresh_token - Application uses the
access_tokento authorised - Server approved the request
access_tokenexpires- Application uses the
access_tokento authorised - Server deny the request
- Application uses the
refresh_tokento get the newaccess_token - Application uses the
access_tokento authorised - Application uses the
access_tokento authorise
Refresh token rotation
To avoid exposing the refresh token, we can rotate the refresh token every single time we receive a refresh token. So the flow happen as below:
access_tokenexpires- Client uses
refresh_tokento get a newaccess_token - Server invalidate previous
refresh_tokenand return newaccess_tokenandrefresh_token- To invalidate, you typically have to either store the last
refresh_tokenper user or keep track of their last one and make sure the new one is different than the last one - Or keep track of expired
refresh_tokento invalidate
- To invalidate, you typically have to either store the last
- Client stores the new
refresh_token