ACL (Access Control Lists)
Cisco router options to filter traffic network.
Notes access list can be defined as number or name
ACL type
Standard — matches on Source IP
Standard ACL ID is
1 -> 991300 -> 1999
Only have the option to completely trust or completely distrust. For example if we have something like this:
Host A -> Router -> Machine A
-> Machine B
If we just want to allow Host A -> Machine A but not Host A -x-> Machine B we cannot do it with the standard mode since it only allows
- Everything from
Host A - Or nothing at all from
Host A
Extended — matches on Source Ip, Destination Ip, Source Port, Destination Port, Protocol
Extended ACL ID is
100 -> 1992000 -> 2699
Provide more fine control comparing to the Standard — matches on Source IP. We can specifically matches Host A -> Machine A only
ACL appication
Only one ACL can be applied
- Per interface
- Per direction
- Per IP protocol
Interface
Keep in mind that if the router is doing NAT (Network Address Translation), the source IP might be different.
For example:
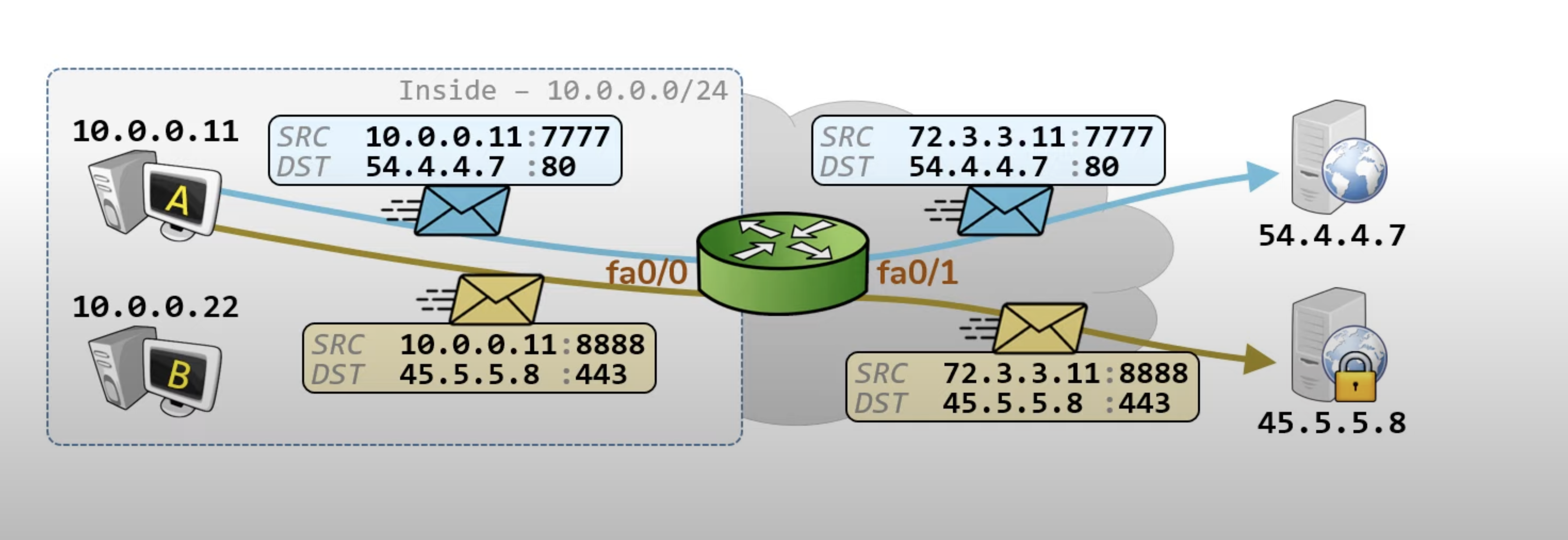
Inside we use 10.0.0.0/24 with interface fa0/0. Therefore the source IP is original. However when going outside of fa0/0 to fa0/1, the src will be translate to 73.3.3.11 which is the router IP.
In this case we need to make sure changing the source IP depends on which interface we apply it to.
Per direction
If it's per direction, we need to make sure we apply to the correct interface as well
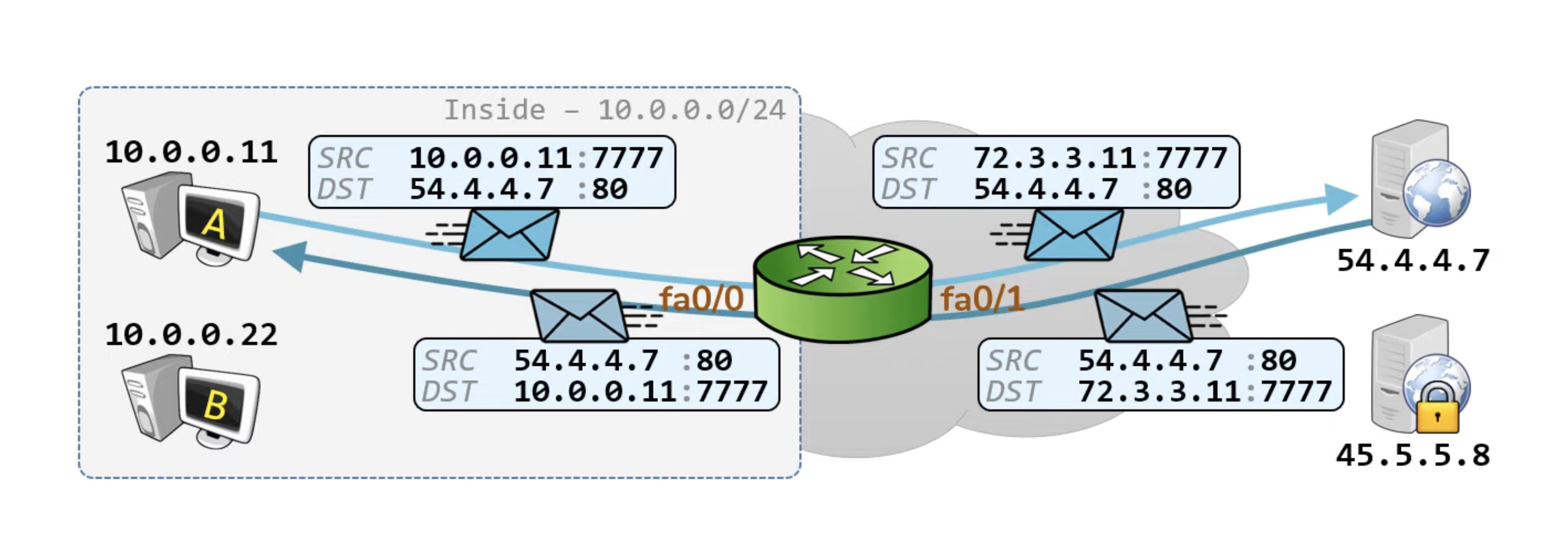
For example, if we want to filter incoming traffic, we want to apply on fa0/1
Per IP protocol
Whether it's IPv4 or IPv6
How to configure access list
We use the syntax:
Standard
access-list <ID> <action> <source> <destination (if extended)>
Extended
access-list <ID> <action> <protocol> <source> <destination>
IDthe ID specified in Standard — matches on Source IP or Extended — matches on Source Ip, Destination Ip, Source Port, Destination Port, Protocol.actionone of the 3:permit: accept trafficdeny: reject trafficremark: comment, when using this the<source>and<destination>will be ignored and becomes free text for you to comment
protocol:ip: matches all IP traffictcpudpicmp
sourceordestinationipaddress:port- Match a subnet
<net id> <wildcard mask>for example192.168.1.0 0.0.0.255 - Match all IP address:
any
Note: the action (permit or deny) will be applied on how you apply the ACL. For example: