Advanced IAM
Some advanced stuff for IAM
Authorisation Model Evaluation
- If there is explicit
DENY, it'sDENY- else, if there is an
ALLOW: thenALLOW
- else, if there is an
- else:
DENY
So by default it's always DENY except for explicit ALLOW
IAM Policies with S3 Bucket Policies
- We take the union of both IAM Policy and S3 Bucket Policy
- Example:
- IAM allow to write to S3, but S3 bucket policy denies
- Cannot write to S3
- IAM deny write to S3 but S3 policy allow write to S3
- Cannot write to S3
- IAM attached but does not specify anything related to S3 Bucket
- S3 policy says read write allow
- So read write allow
- S3 policy says read write allow
- IAM allow to write to S3, but S3 bucket policy denies
Dynamic Policies with IAM
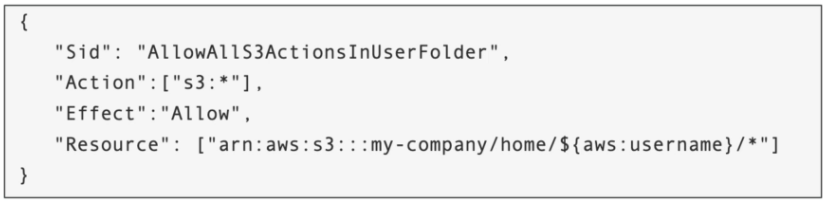
- For example if we want to assign each user a
/home/<user>in S3 bucket - We use policy variable
${aws:username}
Inline vs Managed Policies
- Managed policy
- AWS Managed policy
- maintained by AWS
- Good for power users and administrators
- Updated in case of new services, APIs
- Customer Managed policy
- Best practice, re-useable, can be applied to many principals
- Version controlled, rollback, central change management
- Inline
- Strict one-to-one relationship between policy and principal
- Policy is deleted if you delete the IAM principal
- AWS Managed policy