STS Overview
- Allow to grant limited and temporary access to AWS resources (up to 1 hour)
- Important APIS:
AssumeRole: assume roles within your account or cross account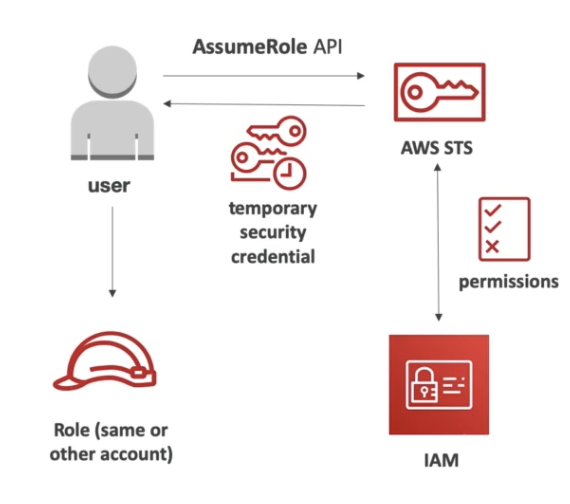
- Define an IAM Role to assume
- Define which principals can access this Role
- Use AWS STS to retrieve credential and impersonate the role
- The credential is valid between 15 minutes to 1 hour
GetCallerIdentity: return details about IAM user or role used in the API callDecodeAuthorizationMessage: decode error message when AWS API is denied. As seen in STS Decode
- Other APIs
AssumeRoleWithSAML: return credentials for users logged in with SAMLAssumeRoleWithWebIdentity: credentials for OAuth login (Facebook, Google, ...) GetSessionToken: for MFA, from a user or AWS account root userGetFederationToken: obtain temporary credentials for a federated user
STS with MFA
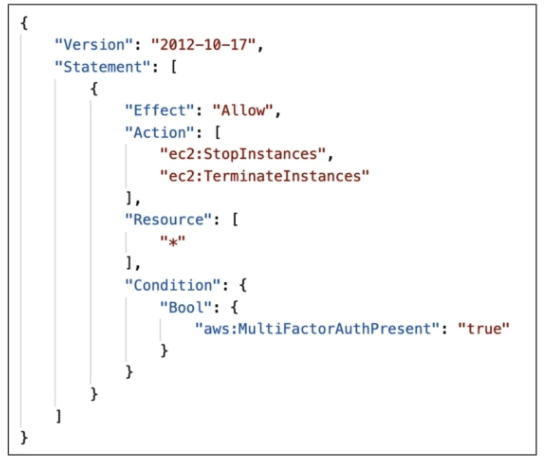
- Use
GetSessionToken from STS, which returns AccessIDSecretKeySessionTokenExpiration
- Use with combination of
"aws:MultiFactorAuthPresent": true in the condition

