Cloudfront Signed URL - Signed Cookies
Distribute premium content for users over the world with CloudFront
We can use CloudFront Signed URL / cookie
- Signed URL: access to individual file
- Signed Cookies: access to multiple file
- Example:
CloudFront-Policy=eyJleHBpcmF0aW9uIjoiMjAyMy0wNy0wOVQxODoxNzowMC4wMDBaIiwia...; CloudFront-Key-Pair-Id=EXAMPLEKEYPAIRID; CloudFront-Signature=abcdefgHIJKLMNOpqr
- Example:
Signed URL vs S3 Pre-signed URL
- Cloudfront Signed URL
- Purpose: Used to grant temporary access to private content served through CloudFront
- Allow access to path, no matter origin
- Account wide key-pair, only the root can manage it
- Can be filter by IP, path, date, expiration
- Leverage caching features
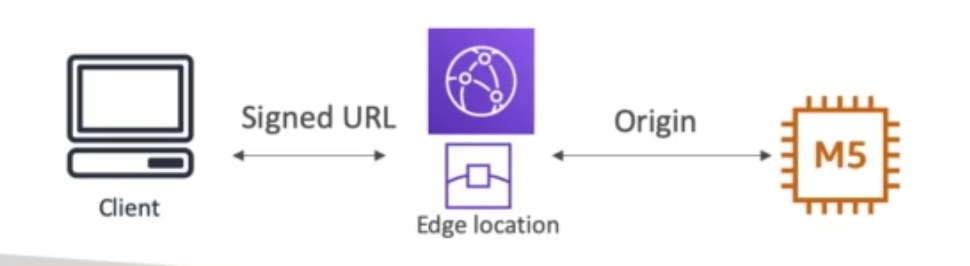
- Example:
https://d12345.cloudfront.net/images/example.jpg?Expires=1665346400&Signature=abcdefghijklmnopqr%3D&Key-Pair-Id=EXAMPLEKEYPAIRID
- S3 Pre-signed URL ^8611ef
- Purpose: Used to grant temporary access to private S3 object directly
- Issue a request as the person who pre-signed URL
- Uses IAM key of the signing IAM principal
- User then have the same permission
- Limited Lifetime

- Example:
https://example-bucket.s3.amazonaws.com/example.jpg?AWSAccessKeyId=EXAMPLEACCESSKEYID&Expires=1665350000&Signature=abcdefghijklmnopqr%3D
- Cloudfront Signed URL
Two types of signers
- Trusted key group (recommended)
- Leverage APIs to create and rotate keys (and IAM for API security)
- You can create one or more trusted key groups
- To do this
- you create your own public / private key
- private key is used by your applications to sign urls
- public key is used by cloudfront to verify urls
- Add the public key to trusted key groups
- you create your own public / private key
- AWS account that contains a cloudfront keypair
- Need to manage using root account and the AWS console
- Not recommeded since you should not use the root account
- Trusted key group (recommended)